Wikileaks: The CIA can remotely hack into computers that aren’t even connected to the internet
Quartz
by Keith Collins
6/24/2017
Excerpt:
When firewalls, network-monitoring services, and antivirus software aren’t enough, there’s always been one surefire way to protect computers that control sensitive operations like power grids and water pumps: cut them off from the internet entirely. But new documents published by WikiLeaks on June 22 suggest that even when such extreme measures are taken, no computer is safe from motivated, well-resourced hackers.
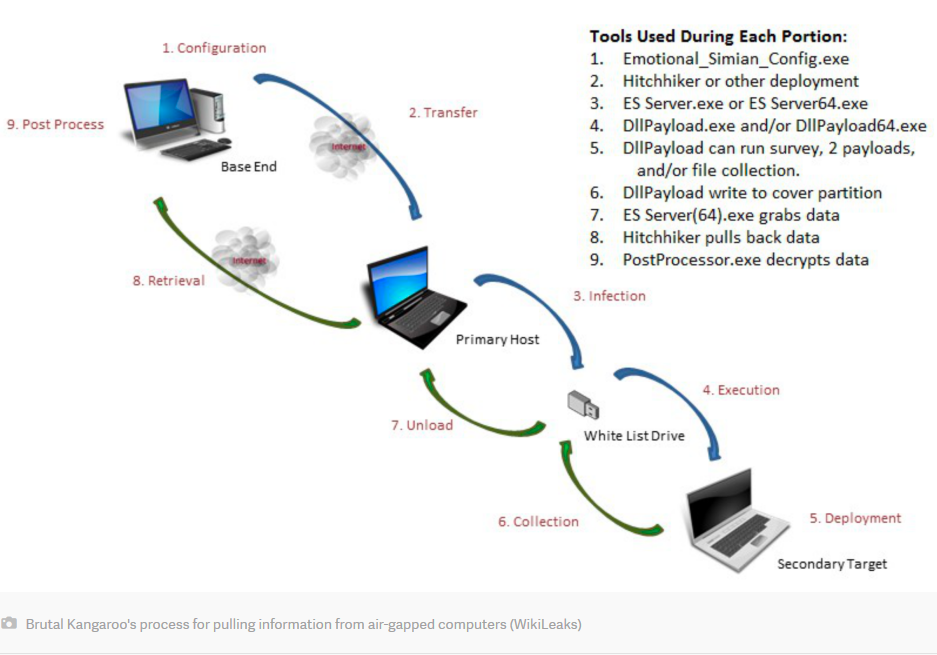
The 11 documents describe a piece of software called “Brutal Kangaroo,” a set of tools built for infiltrating isolated, “air-gapped” computers by targeting internet-connected networks within the same organization. It’s the latest publication in the “Vault 7” series of leaked documents, which describe myriad hacking tools WikiLeaks says belong to the US Central Intelligence Agency (CIA).
Brutal Kangaroo works by creating a digital path from an attacker to an air-gapped computer and back. The process begins when a hacker remotely infects an internet-connected computer in the organization or facility being targeted. Once it has infected that first computer, what the documents refer to as the “primary host,” Brutal Kangaroo waits. It can’t spread to other systems until someone plugs a USB thumb drive into that first one.
Once someone does, malware specific to the make and model of the thumb drive is copied onto it, hiding in modified LNK files that Microsoft Windows uses to render desktop icons, and in DLL files that contain executable programs. From this point, Brutal Kangaroo will spread further malware to any system that thumb drive is plugged into. And those systems will infect every drive that’s plugged into them, and so on, and the idea is that eventually one of those drives will be plugged into the air-gapped computer.
…………………………………………………..
View the complete article including images and links at: